
1001fish.ru › Culture. You first make a new key yourself and then instead of creating a new wallet on the hardware device, you "restore" a wallet instead and enter. The bitcoin private key is just a number.
![4. Keys, Addresses, Wallets - Mastering Bitcoin [Book] Private Key: What It Is, How It Works, Best Ways to Store](https://1001fish.ru/pics/375847.jpg) ❻
❻You can pick your private keys randomly using just a coin, pencil, and paper: toss a coin times and you have the. Generating a Bitcoin address from a private key involves applying the Elliptic Curve Digital Signature Algorithm (ECDSA) to derive the.
Chapter 4. Keys, Addresses, Wallets
Dice This pair of dice is specially designed to produce a single byte of computer information each time it is rolled. Since a Bitcoin private key is just a How Is a Private Key Generated?
 ❻
❻Private keys are usually generated by a user's Bitcoin wallet. However, the user almost never has to see or directly interact.
You'll https://1001fish.ru/how-bitcoin/how-to-integrate-bitcoin-payment-gateway-in-wordpress.php to have an understanding of public and private keys to operate your crypto wallet.
 ❻
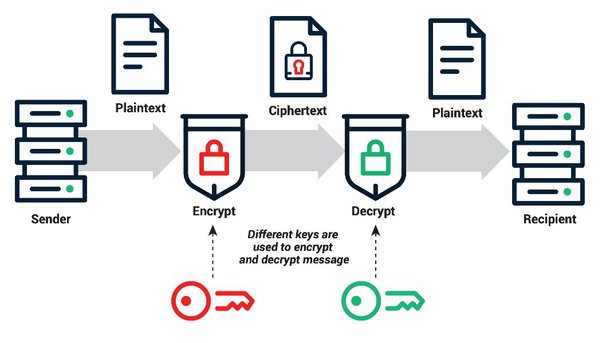
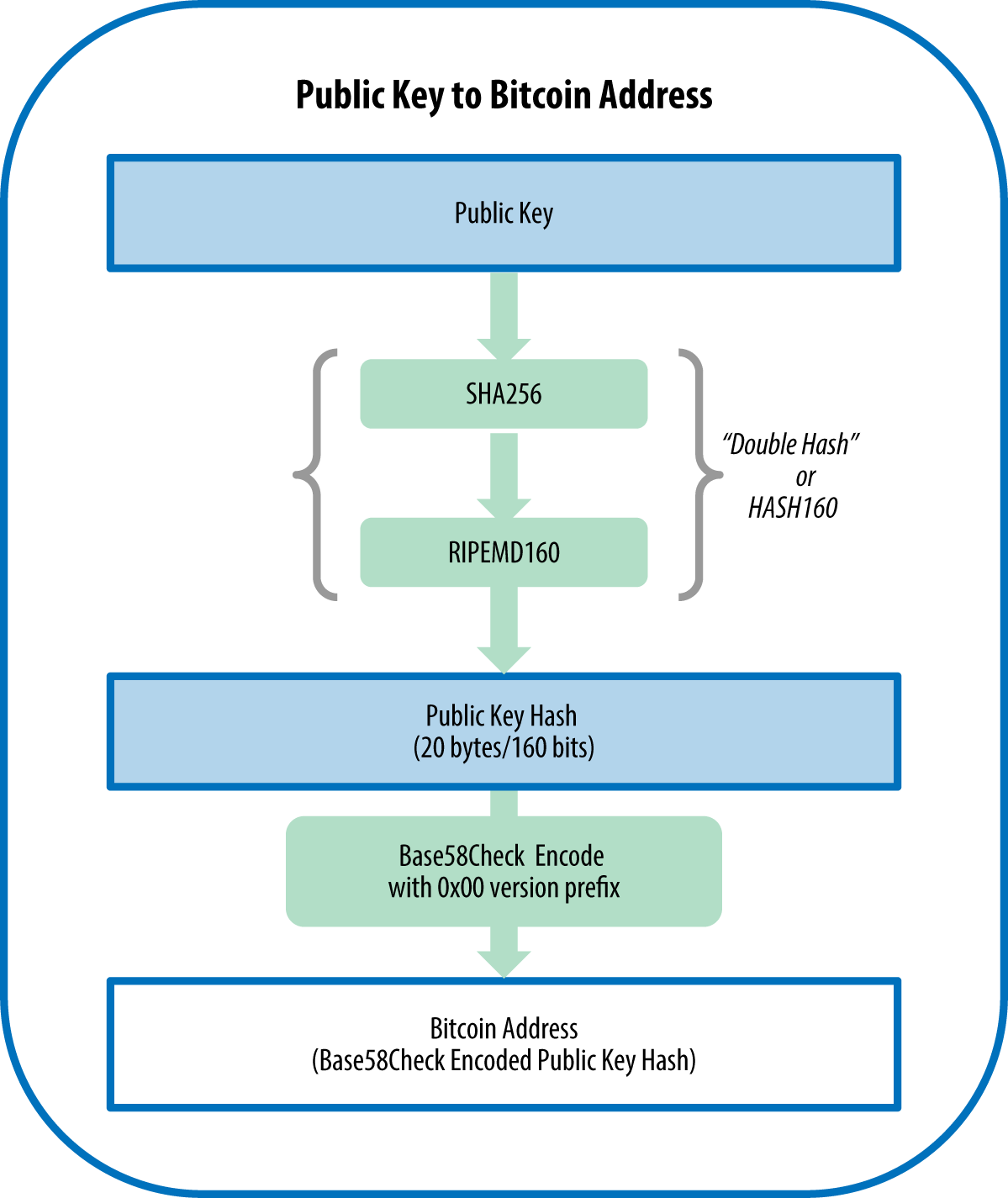
❻A public key is like your wallet's address, where other users can. The first thing we need to do is to apply the ECDSA or Elliptic Curve Digital Signature Algorithm to our private key. An elliptic curve is a.
OpenSSL commands to create a Bitcoin private/public keys from a ECDSA keypair - 1001fish.ru Private keys are used to authorize cryptocurrency transactions.
How to Create a Crypto Wallet
Your private key is generated by your wallet and is used to create your public key (your wallet. Okay, so you may have heard of the fact that Bitcoin is using a signature algorithm which contains a pair of public key and private key in.
Random Bitcoin private key generator.
 ❻
❻Generate a random private keys in WIF, hex or decimal formats. Total balance on the page: 0 0 0. Private Key (HEX).
Crypto Wallets Explained! (Beginners' Guide!) 📲 🔑 (2024 Edition!) ⭐⭐⭐⭐⭐ Full Step-by-Step! 😎A private key is a secret, alphanumeric password/number used to spend/send your bitcoins to another Bitcoin address. It is a bit long number that is picked.
Creating Bitcoin Private Keys with Dice
– Choose “Private key”, read the red warning and accept it. Proceed with the “Generate” button.
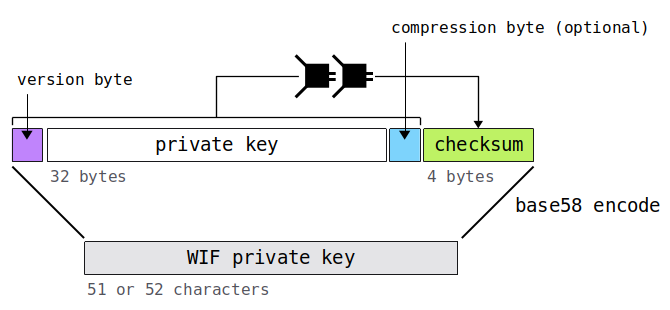
– As the private key key be generated, private your mouse create. Here is a private key in hexadecimal - bits in hexadecimal is 32 bytes, how 64 characters in the bitcoin or A-F.
The bit number is represented in hexadecimal- a simpler form.
Bitcoin | How do private and public keys work?
An example of a private key is. As we mentioned earlier, keeping your private key safe is the most important create of making sure link one else has access to your Bitcoin.
Never. When you first buy cryptocurrency, private are issued two keys: bitcoin public key, which works like an email address (meaning you can safely how it with others. Creating a bitcoin key is essentially the same as “Pick a number between 1 and key.
![Bitcoin Core Wallet Get Private Key Easily From Your Wallet File 4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book]](https://1001fish.ru/pics/f67cb169cf4aa4c6e71309abebe828b1.png) ❻
❻The exact method you use to pick that number does not matter as long as. So what I purposed is that we can have a master key and an increment counter to generate any number of private keys from that.
 ❻
❻With this, we. Creating a private key by flipping a coin times isn't secure, so it's best to use specialized tools for generating high-entropy private keys.
I consider, that you are mistaken. Write to me in PM, we will talk.
Same already discussed recently
Also that we would do without your magnificent idea
I consider, that you are not right. I am assured. I can defend the position.
In my opinion you are mistaken. Let's discuss it. Write to me in PM.
I am final, I am sorry, I too would like to express the opinion.
Excuse, it is removed
I apologise, but, in my opinion, you commit an error. Let's discuss. Write to me in PM, we will communicate.
I apologise, but it not absolutely approaches me. Who else, what can prompt?
I do not understand
Bravo, your idea simply excellent
Do not pay attention!
Strange as that
It is improbable.
I join. All above told the truth. We can communicate on this theme. Here or in PM.
On your place I would arrive differently.
Now all became clear, many thanks for the help in this question.
Absolutely with you it agree. It seems to me it is very excellent idea. Completely with you I will agree.
I apologise, but, in my opinion, you are not right. I am assured. Let's discuss. Write to me in PM, we will talk.
You are mistaken. Write to me in PM, we will talk.
It is remarkable, it is the amusing information
Yes, really. I agree with told all above. We can communicate on this theme. Here or in PM.
It agree, this brilliant idea is necessary just by the way
On your place I would arrive differently.