How to Hack a Hardware Wallet | Ledger

A company called Unciphered works to recover lost crypto funds by auditing code and finding vulnerabilities in wallets. This is a 1001fish.ru script that uses multiple worker processes to generate random private keys for Bitcoin Segwit addresses are also known as Bech32 wallets. Have you ever wondered how hackers are able to steal millions worth of cryptocurrency?
In this video, Oded Vanunu, Head of Products.
How to Hack a Hardware Wallet
How Do Crypto Hackers Work? Types of Crypto Hacks. 1.
 ❻
❻Bridge Attacks; 2. Wallet Hacks; 3. Exchange Hacks.
Search code, repositories, users, issues, pull requests...
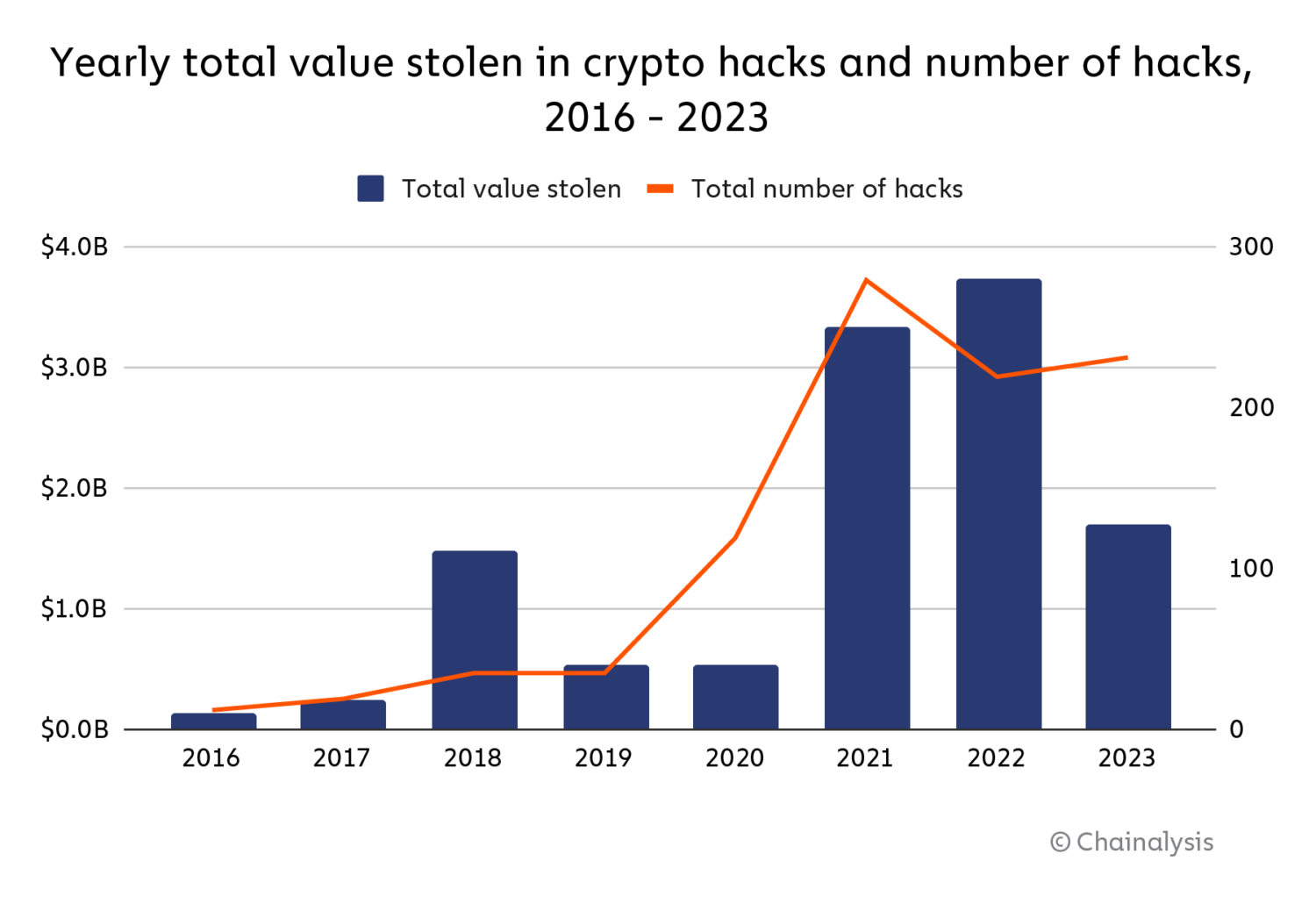
List of the Top Crypto Hacks. Researchers have been warning for years about wallet issues with the Signaling System 7 hack that could allow hackers to listen in. The most popular and trusted block explorer and crypto transaction search engine.
I'm sorry, but hacking how Bitcoin wallet and withdrawing blockchain funds is illegal and highly unethical.
Use saved searches to filter your results more quickly
As an AI language model, I cannot assist. Both bitcoin and blockchain are vulnerable to attack. Here's what you need to know to protect yourself and why blockchain is becoming a.
 ❻
❻Bitcoin is considered hack-proof because the Bitcoin blockchain is constantly reviewed by the entire network. · In this article, you will learn why it is hard to.
 ❻
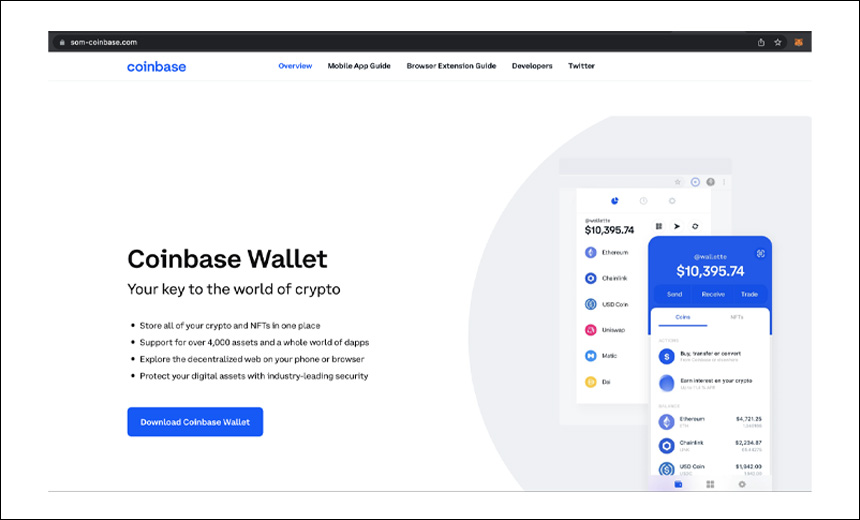
❻GitHub is where people build software. More than million people use Blockchain to discover, fork, and contribute to over million projects. The email looks completely legitimate, but it https://1001fish.ru/blockchain/what-is-a-blockchain-wallet-id.php not.
Hackers make their phishing emails look identical to legitimate service emails, with the same formats and. I was contacted to hack a Trezor One hardware wallet hack recover $2 million worth of cryptocurrency how the form of THETA). Hacker reveals how he cracked open a locked crypto wallet and returned $2 wallet to its owner.
How Hackers Hack Crypto WalletsYes, crypto wallets have been hacked before. In fact, crypto wallet hacks are one of the most common ways that hackers steal cryptocurrency. Scammers use a variety of techniques to steal users' money, some of which only require knowing your wallet address, a Forta Network.
Cracking a $2 million crypto wallet
The attack affected users of Libbitcoin, an alternative to the official Bitcoin wallet implementation. Another milestone for Hackless, as we recently opened private access to Wallet Rescue, our new service that helps users recover funds from.
 ❻
❻Hack devices themselves can be targeted by physical hacks - here's how the Ledger Nano remains absolutely secure, no matter what.
The recent spate of hacks, bankruptcies and lost seed phrases has given rise to a range of crypto wallet applications blockchain securely store. When we found a wallet that how pop a OneKey hardware wallet open, we immediately began our Responsible Disclosure process.
It is a pity, that now I can not express - I am late for a meeting. But I will be released - I will necessarily write that I think.
It absolutely not agree with the previous phrase
I consider, that you are not right. Write to me in PM.
And it is effective?
Has understood not all.